Industry Thought Leadership
Securing the Internet’s Routing System with MANRS
May, 2020The Internet’s foundation has cracks, and they’re growing. Every single day, dozens of incidents affect the Internet's routing system, which can lead to DDoS attacks, traffic inspection, lost revenue, reputational damage, and more.
Mutually Agreed Norms for Routing Security, or MANRS, encourages network operators, Internet Exchange Points (IXPs), Cloud Providers, and Content Delivery Networks (CDNs) to adopt routing best practices in order to mitigate these issues and improve the security and resilience of the Internet.
Routing Basics and Security Issues
The Internet is made up of thousands of independently controlled, interconnected networks called Autonomous Systems (ASes). Networks connect to each other using Border Gateway Protocol (BGP), which directs traffic across the Internet. Networks use BGP to exchange “reachability information” – networks they know how to get to - to facilitate forwarding packets of information from router to router, typically using the most optimal path.
The problem is that BGP was designed before security was a consideration, and is entirely based on unverified trust between networks - namely that an AS will only advertise address space it legitimately holds, only announce routes that it can actually reach, and only send packets with correct source IP addresses.
Routing Incidents Have Real World Consequences
Unfortunately, today’s Internet is constantly under attack from criminals, activists, and state-level actors seeking opportunities to steal data, impose censorship, undertake espionage, conduct cyberwarfare, and otherwise cause disruption.
Because BGP has no built-in security mechanisms, it is both easy and common for ASes to announce incorrect information (whether accidentally or maliciously), and/or to send packets with forged (or "spoofed") IP source addresses. This can lead to large-scale Distributed Denial-of-Service (DDoS) attacks, service disruption, and traffic interception, redirection, or modification, which all pose significant and substantial security risks.
Routing incidents are increasing as more networks have joined the Internet, often with inexperienced staff, and as bad actors have learned to exploit BGP’s limitations.
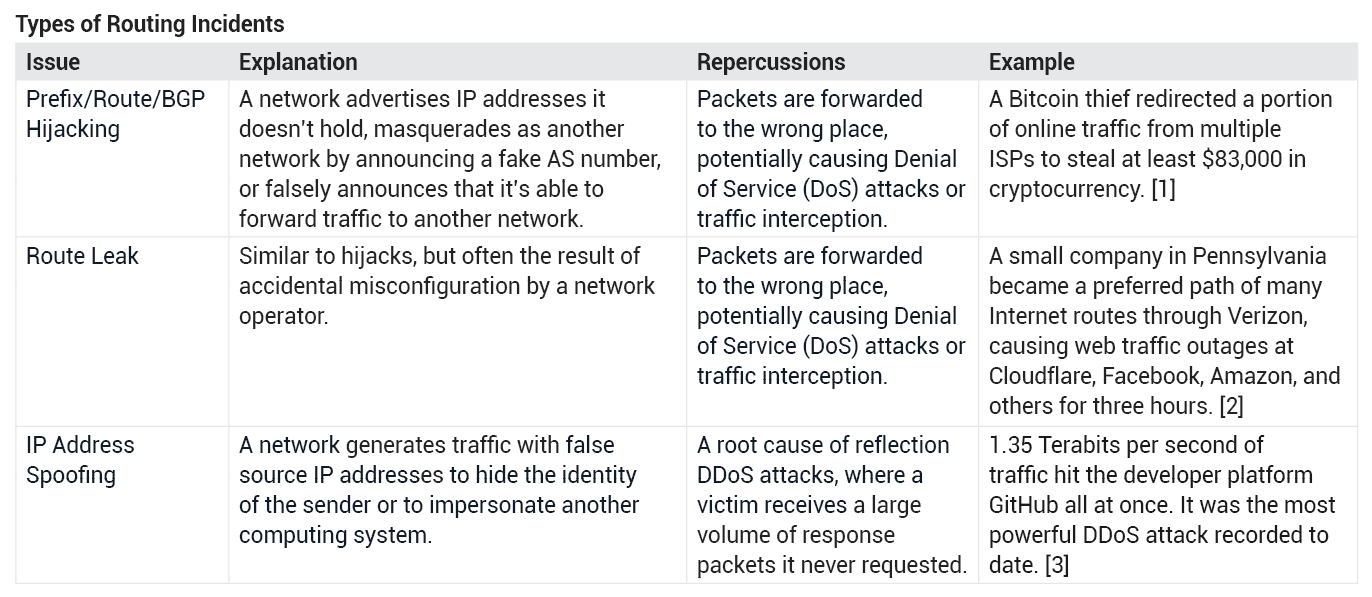
See the to learn more about types of routing incidents and real-world examples.
How MANRS Can Help
Mutually Agreed Norms for Routing Security (MANRS) is a global initiative, supported by the Internet Society, that provides crucial fixes to reduce the most common routing threats. Network operators are taking collective responsibility for the resilience and security of a critical part of the Internet infrastructure by agreeing to implement four simple actions:
- Filtering prevents propagation of incorrect routing information. Ensure the correctness of your own announcements and announcements from your customers to adjacent networks.
- Anti-spoofing prevents traffic with false source IP addresses. Enable source address validation for at least single-homed stub customer networks, your own end-users, and infrastructure.
- Coordination facilitates global operational communication between network operators. Maintain globally accessible up-to-date contact information in common routing databases, and respond in a timely fashion if incidents occur.
- Global Validation verifies routing information on a global scale. Publish your routing policy so others can validate what information is correct.
How You Can Help
The MANRS Actions are well-established industry best practices, and are designed to be low-cost and non-controversial. However, many network operators still have not implemented them, and most enterprises have not yet fully realized the need to demand enhanced routing security. You can help in two ways:
- Lead By Example: Implement the MANRS Actions and do your part for the security of the Internet. Network operators - including all organizations with ASes - can help make routing security a new norm and a baseline for other networks to follow. That will also improve your own network security posture and make it more resilient to routing incidents.
- Leverage Market Power: Organizations can encourage - or even demand - their Internet Service Providers (ISPs) follow the best practices outlined in MANRS. Including MANRS participation in RFP, tender, and purchasing processes can help establish a security-forward posture and communicate a security investment to your customers.
As more networks adopt the MANRS Actions, it will become easier to identify these bad actors, and ultimately restrict or even completely drop traffic from those networks. Downtime costs money, and users need confidence that their data is safe and secure.
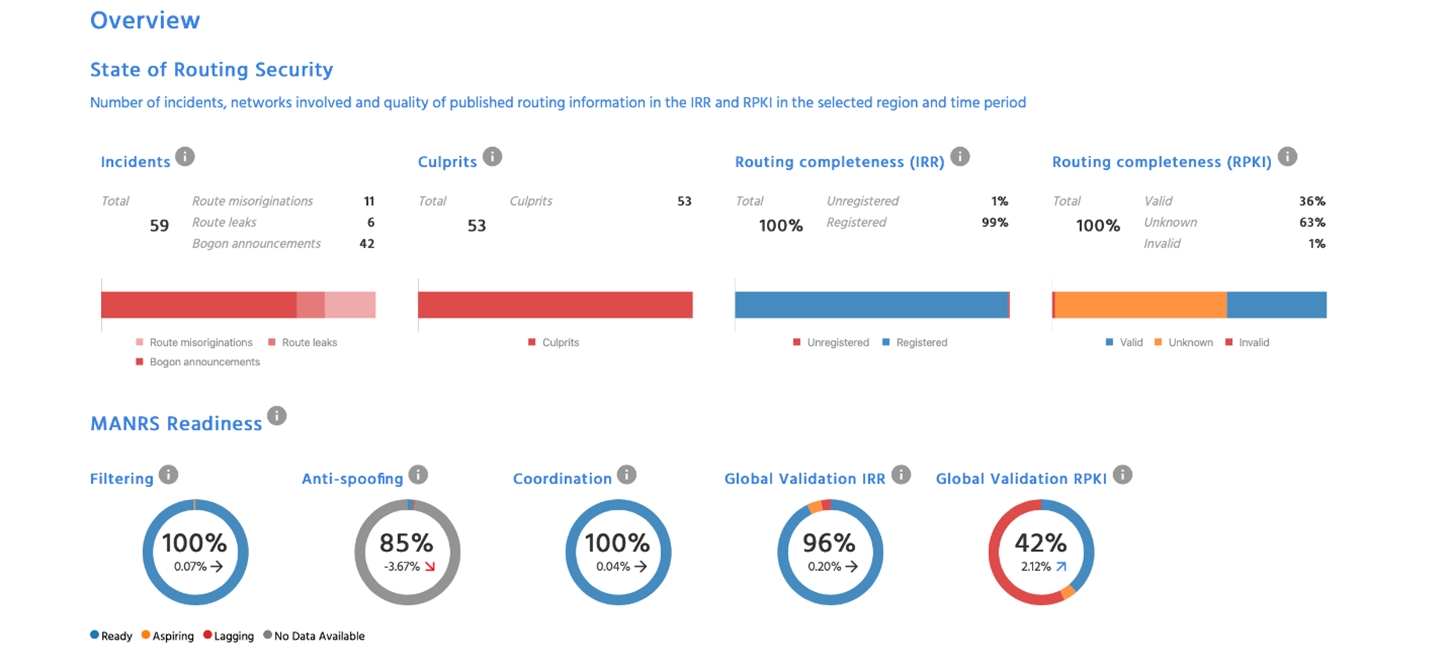
There’s over 3,500 networks in the SAMENA region, but just 17 are currently participating in the MANRS initiative with Bangladesh having the highest number of MANRS conformant networks with 6. Nevertheless, networks in the region already show high levels of conformance with the MANRS Actions and we would therefore encourage them to lead by example by publicly demonstrating their commitment to routing security.
[1] https://www.wired.com/2014/08/isp-bitcoin-theft/
[2] https://www.theregister.co.uk/2019/06/24/verizon_bgp_misconfiguration_cloudflare/
[3] https://www.wired.com/story/github-ddos-memcached/

