Page 104 - SAMENA Trends - February 2020
P. 104
ARTICLE SAMENA TRENDS
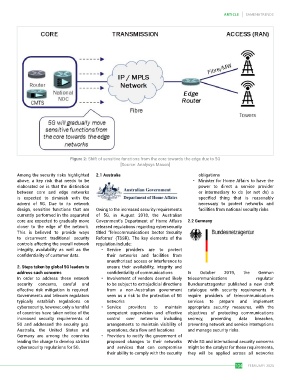
Figure 2: Shift of sensitive functions from the core towards the edge due to 5G
[Source: Analysys Mason]
Among the security risks highlighted 2.1 Australia obligations
above, a key risk that needs to be • Minister for Home Affairs to have the
elaborated on is that the distinction power to direct a service provider
between core and edge networks or intermediary to do (or not do) a
is expected to diminish with the specified thing that is reasonably
advent of 5G. Due to its network necessary to protect networks and
design, sensitive functions that are Owing to the increased security requirements facilities from national security risks
currently performed in the separated of 5G, in August 2018, the Australian
core are expected to gradually move Government’s Department of Home Affairs 2.2 Germany
closer to the edge of the network. released regulations regarding cybersecurity
This is believed to provide ways titled ‘Telecommunications Sector Security
to circumvent traditional security Reforms’ (TSSR). The key elements of the
controls affecting the overall network regulation include:
integrity, availability as well as the • Service providers are to protect
confidentiality of customer data. their networks and facilities from
unauthorised access or interference to
2. Steps taken by global 5G leaders to ensure their availability, integrity and
address such concerns confidentiality of communications In October 2019, the German
In order to address these network • Involvement of vendors deemed likely telecommunications regulator
security concerns, careful and to be subject to extrajudicial directions Bundesnetzagentur published a new draft
effective risk mitigation is required. from a non-Australian government catalogue with security requirements. It
Governments and telecom regulators seen as a risk to the protection of 5G require providers of telecommunications
typically establish regulations on networks services to prepare and implement
cybersecurity, however, only a handful • Service providers to maintain appropriate security measures, with the
of countries have taken notice of the competent supervision and effective objectives of protecting communications
increased security requirements of control over networks including secrecy, preventing data breaches,
5G and addressed the security gap. arrangements to maintain visibility of preventing network and service interruptions
Australia, the United States and operations, data flow and locations and manage security risks.
Germany are among the countries • Providers to notify the government of
leading the charge to develop stricter proposed changes to their networks While 5G and international security concerns
cybersecurity regulations for 5G. and services that can compromise might be the catalyst for these requirements,
their ability to comply with the security they will be applied across all networks
104 FEBRUARY 2020