Page 99 - SAMENA Trends - March-April 2022
P. 99
ARTICLE SAMENA TRENDS
But such attacks are not the only concern
to telecom operators when it comes
to data privacy. PII and customers
financial information are also protected
under multiple data protection laws and
international standards. Starting from
the local data privacy, protection and
classification regulations published by
CITRA in Kuwait as example, up to the
EU General Data Protection Regulation
(GDPR), in addition when it comes to
financial information, the Payment Card
Industry Data Security Standard (PCI DSS)
enforce additional layer and requirements
to implement and comply with.
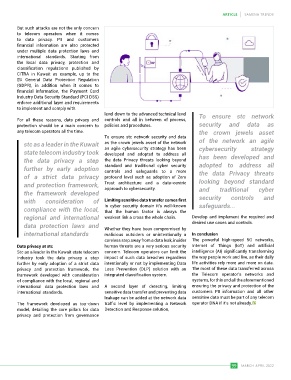
level down to the advanced technical level To ensure stc network
For all these reasons, data privacy and controls and all in between of process,
protection should be a main concern to policies and procedures. security and data as
any telecom operators all the time. the crown jewels asset
To ensure stc network security and data
stc as a leader in the Kuwait as the crown jewels asset of the network of the network an agile
state telecom industry took an agile cybersecurity strategy has been cybersecurity strategy
developed and adopted to address all
the data privacy a step the data Privacy threats looking beyond has been developed and
further by early adoption standard and traditional cyber security adopted to address all
controls and safeguards to a more
of a strict data privacy profound level such as adoption of Zero the data Privacy threats
and protection framework, Trust architecture and a data-centric looking beyond standard
approach to cybersecurity.
the framework developed and traditional cyber
with consideration of Limiting sensitive data transfer comes first security controls and
compliance with the local, In cyber security domain it’s well-known safeguards...
that the human factor is always the
regional and international weakest link a cross the whole chain. Develop and implement the required and
data protection laws and Whether they have been compromised by desired use cases and controls.
international standards malicious outsiders or unintentionally a In conclusion
careless step away from a data leak, insider The powerful high-speed 5G networks,
Data privacy at stc human threats are a very serious security Internet of Things (IoT) and artificial
Stc as a leader in the Kuwait state telecom concern. Telecom operators can limit the intelligence (AI) significantly transforming
industry took the data privacy a step impact of such data breaches regardless the way people work and live, as their daily
further by early adoption of a strict data intentionally or not by implementing Data life activities rely more and more on data.
privacy and protection framework, the Loss Prevention (DLP) solution with an The most of these data transferred across
framework developed with consideration integrated classification system. the Telecom operator’s networks and
of compliance with the local, regional and systems, for this and all the aforementioned
international data protection laws and A second layer of detecting, limiting ensuring the privacy and protection of the
international standards. sensitive data transfer and preventing data customers PII information and all other
leakage can be added at the network data sensitive data must be part of any telecom
The framework developed as top-down traffic level by implementing a Network operator DNA if it’s not already.
model, detailing the core pillars for data Detection and Response solution,
privacy and protection from governance
99 MARCH-APRIL 2022